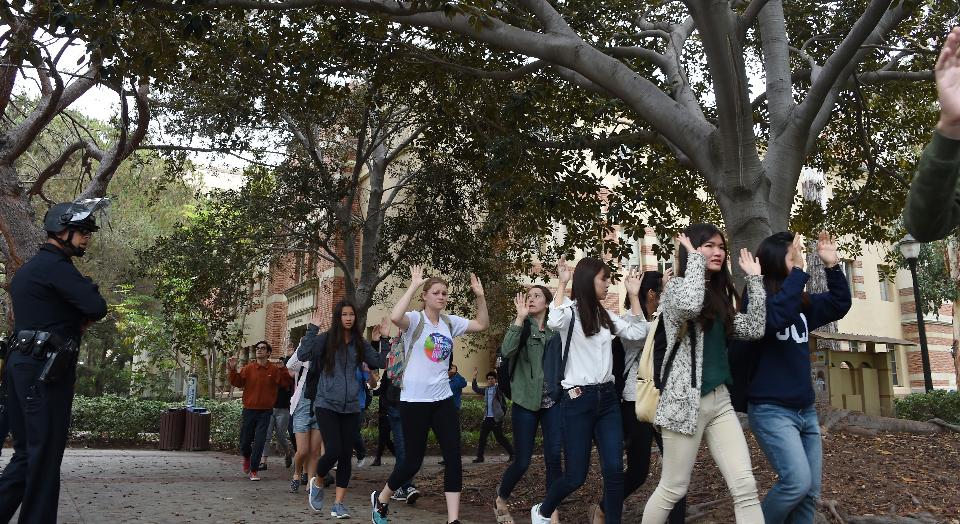by Robert Whitcomb | Jun 10, 2016 | AI World Society Summit
(June 13th, 2016) A fascinating article in The Harvard Gazette tells how the Chinese government “fakes 448 million social-media posts a year in a strategy that seeks to create the appearance of ‘viral’ outbursts of Web activity, according to a new study by Harvard data scientists.’’

Gary King is the Albert J. Weatherhead III University Professor at Harvard University, based in the Department of Government. He is pictured in the CGIS Knafel Building. Stephanie Mitchell/Harvard Staff Photographer
“The posts appear under the names of apparently ordinary people, and aim to distract from topics related to actual or potential collective action, said Gary King, the Albert J. Weatherhead III {Harvard} University Professor, who carried out the research with two of his former graduate students….’’
“The research shows that assumptions about the Chinese government’s tactics in this area are wrong, King said. The prevailing belief among journalists, academics, and activists, he said, has been that the government maintains an aggressive social media strategy that actively rebuts anti-government posts and tries to cast opponents, whether domestic or foreign, institutional or individual, in a negative light.
“In fact, such posts make up a tiny minority, the researchers found. Most qualify as ‘cheerleading’: praise for the government and items on revolutionary history, national holidays, and other patriotic themes. In short, King said, the government is trying to distract people, and defuse tension over fraught issues.’’
To read the whole article, hit this link.

by Robert Whitcomb | Jun 5, 2016 | AI World Society Summit
(June 6th, 2016) Leaders at the G7 Summit approved the first international stand-alone agreement on cybersecurity, including data protection and Internet governance. A number of organizations, including the Boston Global Forum (BGF), submitted recommendations to the leaders for their consideration. The BGF’s recommendations included what it calls the Ise-Shima Norms for cyberbehavior, which builds on the BGF’s Ethics Code of Conduct for Cyber Peace and Security (ECCC). (Ise-Shima is the Japanese region where this year’s summit was held on May 26-27.)

World leaders attend the G7 2016 Ise-Shima Summit in Japan.
The BGF’s recommendations were part of its BGF-G7 Summit Initiative.
“We endeavor to develop policy frameworks that further promote effective privacy and data protection across jurisdictions to meet high standards of privacy and data protection,” according to a statement of principles in the G7 leaders’ agreement.
“We also welcome proactive approaches such as ‘Privacy by Design,’ which take privacy and protecting personal data into account throughout the engineering process. We recognize that protecting privacy and enhancing cybersecurity help ensure business and consumer trust and promote innovation crucial to our economic growth.”
“It sounds innocuous, but it’s not. It’s actually very significant,” John Savage, An Wang Professor of Computer Science at Brown University, told Roll Call’s Paul Merrion. Professor Savage is a BGF member who helped draft the Ise-Shima Norms.
“It’s progress, it’s recognition that nations need to help one another.”
The agreement also states that “no country should conduct or knowingly support ICT (information and communication technology)-enabled theft of intellectual property, including trade secrets or other confidential business information, with the intent of providing competitive advantages to its companies or commercial sectors.’’
It continued: “We commit to facilitate the free flow of information to ensure openness, transparency and freedom of the Internet, and a fair and equal access to the cyberspace for all actors {in the} digital economy while respecting privacy and data protection, as well as cybersecurity.’’
Further, the G7 affirmed: “We continue to support ICT policies that preserve the global nature of the Internet, promote the flow of information across borders and allow Internet users to access online information, knowledge and services of their choice. We oppose data localization requirements that are unjustifiable, taking into account legitimate public policy objectives.”
Professor Savage told Mr. Merrion: “That’s directed at the Chinese and Russians, but mostly the Chinese.” While it doesn’t directly and immediately affect these countries, “it’s a talking point,” he told Mr. Merrion

by Robert Whitcomb | Jun 3, 2016 | AI World Society Summit
(June 6th, 2016) We at The Boston Global Forum were very pleased that the G7 leaders at their May 26-27 summit in Japan included in their final declaration an important statement on cybersecurity. BGF experts had submitted to the leaders the BGF’s Ise-Shima Norms for cyberbehavior (named after the region where the summit was held).

The BGF’s recommendations were part of the BGF-G7 Summit Initiative.
Among the leaders’ comments on cybersecurity:
“We strongly support an accessible, open, interoperable, reliable and secure cyberspace as one essential foundation for economic growth and prosperity.’’
The leaders also announced initiatives on improving the global economy through coordinated fiscal and monetary policies; on migration and refugees; on trade; on infrastructure; on health; on improving the condition and status of women; on battling political and other corruption; on climate change, and on energy, including decarbonization.
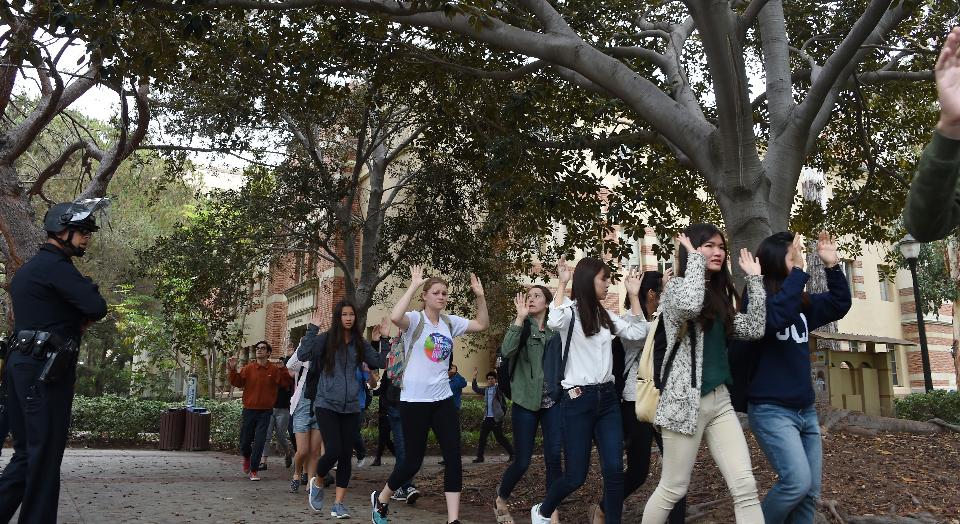
by Robert Whitcomb | Jun 3, 2016 | AI World Society Summit
(June 6th, 2016) There are some lessons from cybersecurity that can be used to improve on-campus physical security, writes John Vallasenor in the wake of the recent murder/suicide on the campus of the University of California at Los Angeles.
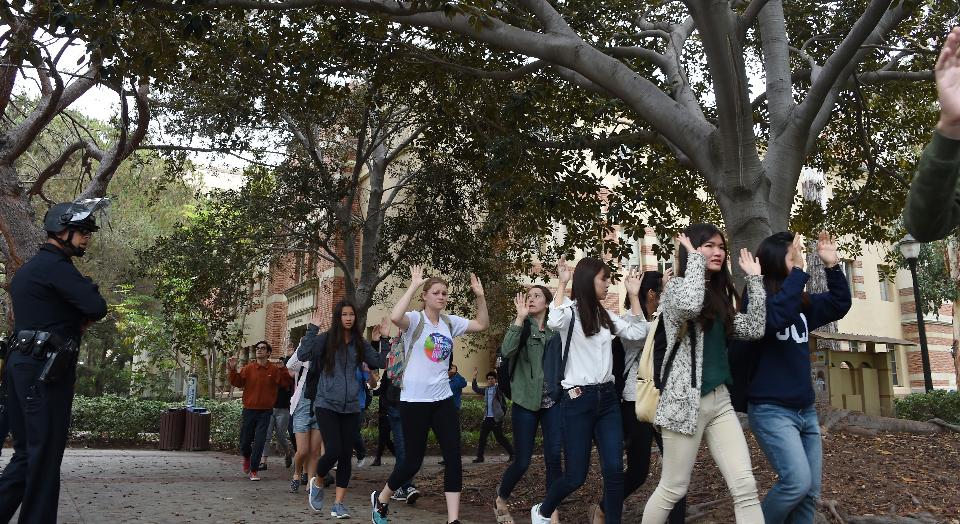
Among them are:
- “Create a mechanism for disseminating critically important alerts, and don’t clutter it with less important messages.’’
- “Have the ability to control access points.’’
- “Before an emergency arises, fully test emergency responses to find gaps.’’

by Robert Whitcomb | Jun 3, 2016 | AI World Society Summit
(June 6th, 2016) Major Gen. Stephen Day, the former head of Cyber and Information Security at the Australian Signals Directorate, says that a trusted and ethical cybersecurity industry is vital to Australia’s socio-economic well being and national security.

General Day discussed America’s heightened awareness of cyberattacks; that there is a real concern about the threat of an attack in the U.S., in stark comparison to Australia.
“Out of this {the U.S.} atmosphere, one tinged with a little bit of fear, has arisen some less-than-honorable businesses and business practices. There is a risk that the reputation of the cybersecurity industry could be harmed, and if that happens then the industry will be kept at arm’s length, and that is in no one’s interests.”
“If you are a cybersecurity vendor and you have a single technical product offering, do the right thing and explain to your customers that your offering will work best when it is part of a bigger plan,” he said. “If you are a consumer of cybersecurity products, and you have a vendor that insists that they have a single silver bullet solution, then you’re probably best off showing them the door.”
by Robert Whitcomb | May 28, 2016 | Initiative
(May 30th, 2016) Pavan Duggal, an Indian cyberlaw and cybersecurity expert, warned that as governments around the world struggle to stop cyberattacks and data breaches, India needs to come up with a more comprehensive legal approach and framework to address various issues in cyberspace. Read this link to The Times of India story.

“Today, a lot of work in personal, professional, social and governance space is being done on the internet. Therefore, there is a need to look at the issues in cyberspace. It is here that issues like cyberlaw, cybercrime and cybersecurity come in,” Mr. Duggal, president of cyber laws.net and a lawyer who argues before the Indian Supreme Court, said at meeting on cyberlaw, cybercrime and cybersecurity in New Delhi.
He warned that, given recent cyberspace trends in India, cyberterrorism and political radicalization via the Internet are going to hit big time in India.
by Robert Whitcomb | May 26, 2016 | AI World Society Summit
The biggest issues at the G7 Summit have been how to get the global economy humming again; the refugee crisis in Europe and the Mideast; Chinese expansionism in the East and South China Sea, and cybersecurity. Read this link.
The last item has been a priority of The Boston Global Forum this year. BGF experts have presented their proposals on how to improve cybersecurity in particular and cyberbehavior in general to the G7 leaders. Indeed, a key part of the BGF’s BGF-G7 Summit Initiative is its Ise-Shima Norms for cyberbehavior, named for the location of the summit.
As for the refugees: European Council President Donald Tusk said on Thursday he would seek G7 support for more global aid for them.
“If we (G7) do not take the lead in managing this crisis, nobody would,” Mr. Tusk told reporters. A flow of migrants to Europe from Syria, other parts of the Mideast and Africa confronts the continent with its biggest refugee crisis since World War II.
In a closing communiqué, leaders were also expected to cite the importance of maritime security, including calling for respect for the rule of law and opposition to provocative acts that try to change the status quo by force – in a clear reference to Chinese expansionism.
Although full agreement on macro-economic policy looks difficult, the G7 leaders are expected to promote monetary, fiscal and infrastructure policies to spur growth in the final summit communiqué.
Britain and Germany are resisting calls for fiscal stimulus, and so Japanese Prime Minister Shinzo Abe will urge the G7 leaders to adopt a flexible fiscal policy, taking into account each country’s economic and political situation.